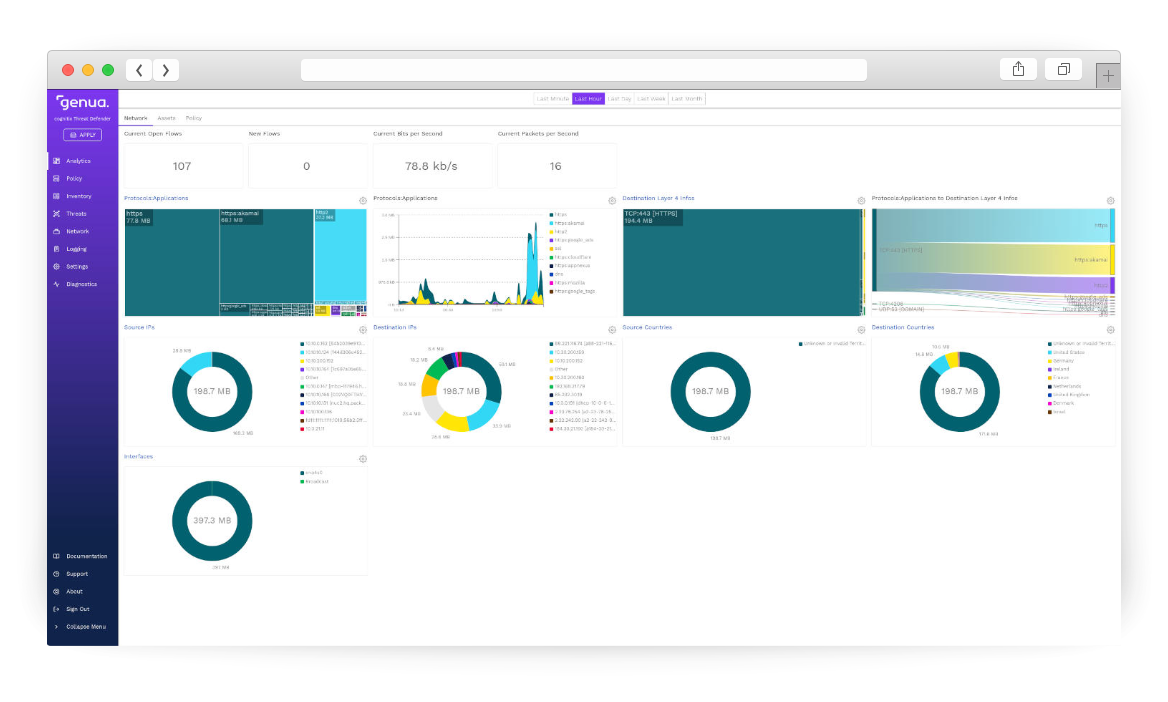
Insights
Zero Trust Architectures for the Industry
Many industrial plants are managed by external machine manufacturers or have connections to externally managed services, for example for cloud computing. For the industry, this means an increasing loss of control. Zero Trust architectures from the IT world help operators retain network sovereignty over their OT, thereby regaining trust in their infrastructure and operational technology.
The digitization does not stop at operational technology (OT) in industrial environments. More and more critical processes are being digitized, and sensitive data and systems are being networked. This drastically increases the complexity of infrastructures. At the same time, dependency on digital processes is increasing, resulting in increasing demands on availability and reliable function.
To date, the traditional approach to managing digital infrastructure has been centrally managed networks with a uniformly high level of security. Since compromising individual parts endangered the security of the entire network, this had to be avoided at all costs, for example through strong separation from other networks. In today's networks, however, more and more systems are managed by external manufacturers and service providers or have the necessary connections to externally managed networks, for example for edge or cloud computing. This leads to an increasing loss of control over one's own network: The traditional approach does not scale with the reality of the networks and the increased requirements for availability and reliability.
What Does "Zero Trust Networking" Mean?
In the Zero-Trust Networking paradigm, trust in the security of the entire network is replaced by trust in the security of specific communication endpoints, i.e. devices, services, and applications. A compromise of individual endpoints is thus limited to the permitted communication relationships and no longer endangers the entire network. This approach gives the operator back control of his systems and proactively reduces the attack surface. Reactively, it also allows faster detection and limitation of damage as well as rapid and targeted recovery. The result is more robust and resilient networks, suitable for the higher criticality and the associated requirements for reliability and control.
Microsegmentation: Forrester's Zero Trust Networking
Forrester's Zero Trust Networking divides an existing network within itself by deploying firewalls at strategic locations into microsegments, between which communication is regulated. In the extreme case, each device in the network is in its own microsegment. This approach lends itself well to post-hardening of existing networks and works well with legacy applications. However, a dynamic mapping between identities and IP addresses may be required, since only these are reliably visible as a decision-making criterion in data traffic.
Similar to this network-based microsegmentation is host-based microsegmentation, in which centrally managed agents on each device limit its communication with other devices. However, these agents typically have to invasively intervene in the system to perform their tasks and run with high privileges. This may affect the reliability of the systems and, in the worst case, create an additional target for attack.
Sample Implementation for Mesh-Based Microsegmentation
A reliable implementation of the network-based microsegmentation can be achieved with the cognitix Threat Defender. This integrates transparently into the network like a switch, but allows granular, dynamic and cross-context regulation of the data streams. In contrast to switches with Network Access Control (NAC) or many firewalls, the control and restriction does not only take place at the network level, but also at the application level. These capabilities are supplemented by an integrated Intrusion Detection System (IDS) and the use of Indicators of Compromise (IOC), i.e. artefacts that indicate a compromise. Their results can in turn be included in the access rules. This makes it possible, for example, to isolate potentially infected systems in real time or to restrict their communication in order to be able to detect attacks early and react appropriately in good time.
Software Defined Perimeter
The Zero Trust Networking concept of the Cloud Security Alliance (CSA) is a Software Defined Perimeter (SDP), which allows external clients to access an internal infrastructure after authentication. In contrast to a classic Virtual Private Network (VPN), there is no complete network coupling here, but access is limited to individual services. The CSA's original proposal defines a special tunnel protocol for encrypting and transmitting identities, which the clients must implement. This complicates the connection of legacy applications. Alternative implementations using VPN technologies simplify this since the tunnel is implemented transparently at the network level and not at the application level.
Example: Software Defined Perimeter Using Remote Maintenance
A solution based on the concept of the Software Defined Perimeter is the remote maintenance solution genubox from genua. A service box from the internal network connects to a rendezvous server – the software defined perimeter – that can be reached by the external remote operator. The remote maintainer, in turn, uses the remote maintenance app to establish encrypted communication with this perimeter. After successful authentication, access to specific services is enabled, such as the desktop of the machine to be maintained, the terminal (via SSH) or selected ports. There is no network coupling. In accordance with the increased requirements for security and compliance in the industrial environment, a video recording of the desktop or the SSH connection also takes place and transferred files are checked for malware. These recordings can also be called up later.
Google's BeyondCorp for Web-Based Applications
With BeyondCorp, Google has presented an implementation of Zero Trust Networking, in which control takes place directly on the service via an upstream Identity Aware Proxy (IAP). The connection between client and IAP is encrypted via HTTPS. This approach is very well suited for web-based applications and offers high and simple scalability. However, applications that are not inherently web-based can only be integrated cumbersomely via web-based tunnels or not at all. In the industrial environment, this approach is therefore only of limited use.
In summary, it can be said that Zero Trust networking is also a suitable security paradigm in the industrial environment in order to achieve a high level of robustness and resilience in highly networked, sometimes security-critical infrastructures. The administrator regains control of his infrastructure, even if it is partly managed by someone else and connected to external networks. Zero Trust Networking thus increases trust in the availability and security of IT/OT networks, which form the basis of industrial value-added processes. The answer to the question of which Zero Trust approach should be implemented ultimately depends on the specific framework conditions and should be discussed with an IT security expert.





![[Translate to English:] [Translate to English:]](/fileadmin/_processed_/b/b/csm_genubox-visual_2efc2755a7.png)
![[Translate to English:] [Translate to English:]](/fileadmin/_processed_/5/2/csm_cyber-diode-visual_61b0b2e474.png)