Case Study
Keep a Close Watch on Internal Network Traffic
Simple IT security solutions used up to now often have weaknesses and cyber attacks remain undiscovered for longer periods of time. IDS/IPS systems therefore make sense but they are complex and costly to administer. The Berlin-based IT service provider datenhain GmbH takes a different approach: With the practical cognitix Threat Defender from genua, data traffic is monitored in real time to detect and defend against dangers within networks, thereby providing additional IT security from behind the perimeter firewalls.
"Previous security concepts place the primary focus on keeping attackers out of one's own network. The internal network, on the other hand, is trusted and network traffic is only rarely monitored and analyzed"
André Hermbusch, General Manager, datenhain GmbH
datenhain GmbH: IT Security Services for Companies
For more than 10 years, datenhain GmbH has been advising and supporting small- and medium-sized enterprises on the topics of IT infrastructure and IT security. The problem: increasingly sophisticated and well-concealed attack methods frequently use standard protocols, are often encrypted and not detected by signature-based systems with static rules. Malware can thereby spread in the internal network. This is a current topic in particular for critical infrastructures, development-intensive companies and other highly sensitive areas. "Many of our customers must satisfy compliance regulations with increased security requirements. We therefore searched for a practical and easy-to-integrate solution that would also allow us to keep an eye on internal network traffic," says André Hermbusch.
Real-Time Network Traffic Monitoring and Automatic Defense
The IT service provider had been searching for a state-of-the-art solution for network analysis. Based on datenhain's experiences, normal network sniffers were no longer adequate for the increasingly complex network relationships and rapidly growing network traffic. The solution needed to above all monitor communication of the end devices with the internet, with internal servers and devices among one another. "We need machine logic that analyzes the network traffic, identifies dangers in real time and automatically implements rules for defending against attacks. Customers often want graphically prepared overviews so that they can immediately zoom in on points of interest," says the General Manager, describing his requirements. While intrusion detection systems (IDS) and intrusion prevention systems (IPS) can detect anomalies in network traffic and automatically prevent attacks, many companies lack the resources and the time to intensively deal with such tools.
cognitix Threat Defender Uses Data Analytics and Threat Intelligence
The IT service provider became aware of cognitix Threat Defender from genua through a test performed by heise.de. The software solution combines the IDS approach with prevention functions. Using data analytics and threat intelligence, cognitix Threat Defender detects attacks in real time and also offers a platform for the use of AI technologies.
"We tested cognitix Threat Defender and were surprised how quickly we received the first real-time overview of the network traffic. Following the base installation of the software, a standard set of rules is already available that provides an overview of the network and the installed devices," says André Hermbusch, describing his first impression. datenhain typically uses cognitix Threat Defender for applications such as detecting the horizontal propagation of malware, e.g., encryption trojans, in normal office networks. In factory halls with technical devices from many different manufacturers, monitoring is performed to determine whether devices contact one another in the event that this deviates from normal behavior. Moreover, the network traffic is divided into classes so as to prevent undesired protocols or to detect undesired traffic such as YouTube or Facebook.
cognitix Threat Defender detects the behavioral patterns of the network devices and assigns them defined rules. Previously separate functions, such as network analysis, intrusion prevention, asset tracking and a dynamic policy engine, are thereby merged into a single system.
Security Defined Networking Guarantees a High Protection Level
Cognitix Threat Defender sets up a self-monitoring, secure network (Security Defined Networking) that detects the behavioral patterns of the network devices and assigns defined rules. Previously separate functions, such as network analysis, intrusion prevention, asset tracking and a dynamic policy engine, are thereby merged into a single system. cognitix Threat Defender analyzes the network traffic according to IP and MAC addresses, ports, protocols and applications of OSI layers 2 to 7. Traffic is thereby checked for problematic addresses, domains or file signatures which should be detected and blocked. In addition, an asset database of all devices in the network is created and the communication relationships of the devices examined.
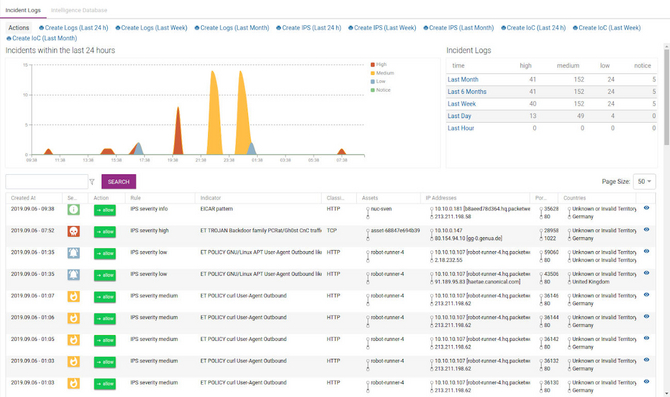
The devices are assigned behavioral rules and these are monitored. Any new devices that appear are immediately reported. Real-time reporting with a traffic-light system provides messages about a possible potential danger. Using drill-down reporting, suspicious areas can be considered in greater detail by clicking on a graphical representation of the network traffic. Information such as the live data from the filtered area is thereby available with a one minute advance to examine the participating devices and target addresses.
Simple Integration in the Network without Sacrificing Performance
"When we come into a company, we first examine the current state of the network to obtain an overview of the existing infrastructure,” reports André Hermbusch. During this process, the network traffic is initially scanned passively and a picture of the "normal state" made. By taking a starting inventory of the network in this way, general weak points and security holes are detected that could be caused, e.g., by configuration errors, network problems or outdated device software.
Compared to other IDS systems, the General Manager describes the installation of the software and the integration in the network as being uncomplicated. Integration can be performed without needing to make changes to the network topology. Rules about the "normal behavior" of the network traffic are defined on the basis of the starting inventory. A policy engine manages the rules. They determine how to respond to undesired behavior or acute dangers. If, for example, a device establishes a connection with more than ten hosts within one minute, a rule can ensure that the device is isolated.
Based on datenhain's experience, the continuous monitoring of network traffic is a big challenge for performance: "cognitix Threat Defender is a pure software solution. In terms of hardware, all that is needed is – depending on the application – a cigarette pack-sized mini-PC or a powerful server for the real-time analysis of 40 Gbit/s network traffic. The network analysis has only a minimal affect on latency. cognitix Threat Defender achieves nearly switch-level performance."
Increased Security: Detect and Eliminate Undesired and Dangerous Traffic
André Hermbusch reports that during the initial analysis of the communication relationships, unexpected details regularly emerge. As an example, he mentions a television that establishes a connection with its manufacturer in China every morning or an old production system that has received no security updates in eight years and would be easy to attack. A Windows PC that has not been used in a long time, on the other hand, would be identified as being infected due to its unusual traffic. Also visible was the banned private use of Facebook within a company, which cognitix Threat Defender can prevent through policy rules or greatly slow down in network traffic. André Hermbusch also comments positively on the short release cycles for cognitix Threat Defender for the implementation of customer requests.
cognitix Threat Defender takes a big step in early 2020. genua will then offer the security platform on its own hardware which can easily be inserted in networks as an appliance.